The Ticking Clock for American Checkout Pages
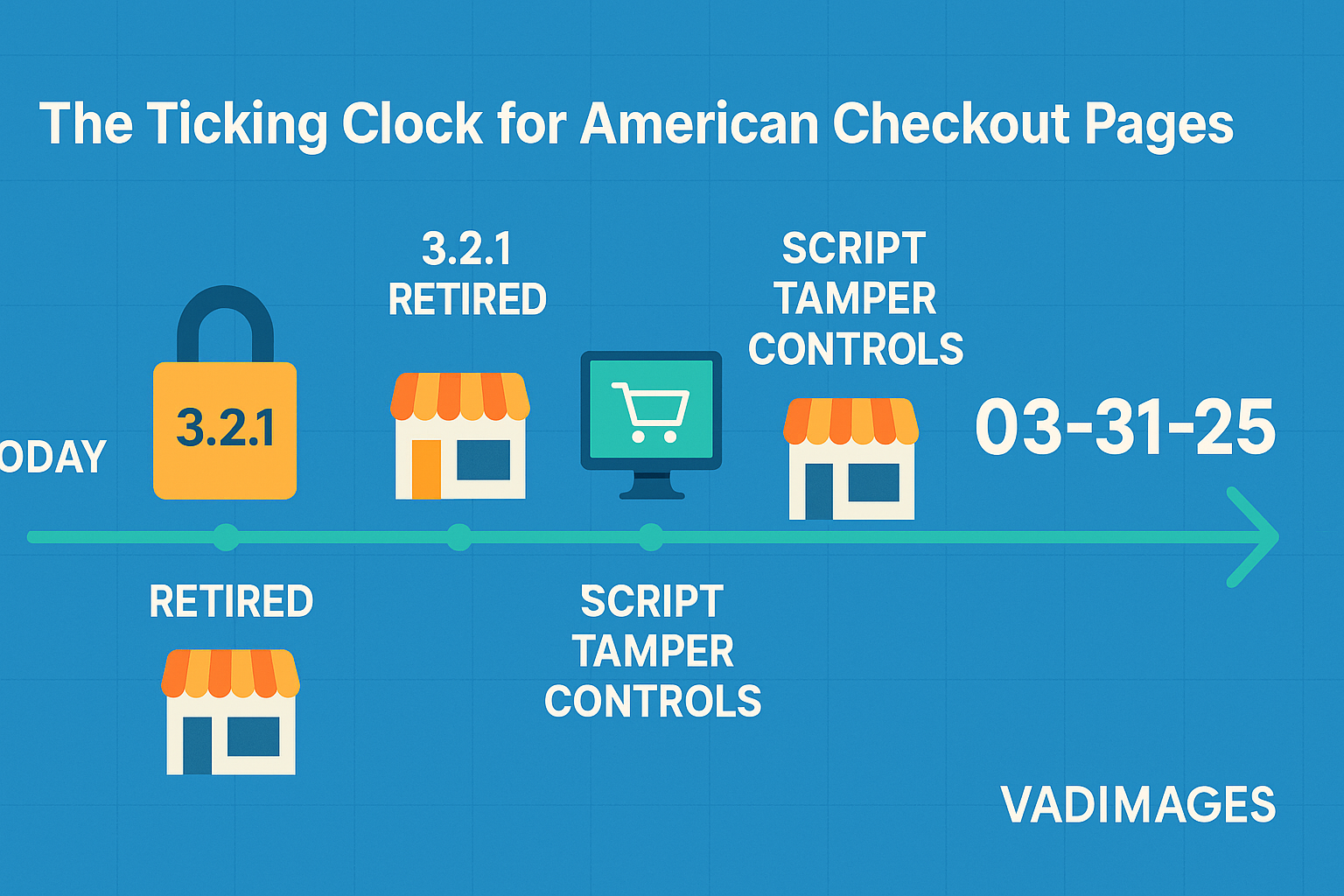
The Payment Card Industry Security Standards Council did not choose its dates lightly. When version 3.2.1 officially sunsetted on December 31 2024, tens of thousands of Main-Street retailers and direct-to-consumer brands suddenly discovered they were standing on a compliance cliff. They now have until March 31 2025 to implement the sixty-four “future-dated” controls baked into PCI DSS v4.0.1—controls that will shift overnight from recommended best practice to mandatory pass-or-fail yardsticks.
Because U.S. acquirers already warn that penalty schedules will match those applied to large enterprises, the countdown is more than academic. Supplemental fines can run as high as five thousand dollars per month for each non-compliant merchant ID. Worse, card brands reserve the right to increase interchange rates or revoke processing privileges entirely, a threat few growth-stage e-commerce operators can absorb. For small businesses, the deadline feels less like an exercise in paperwork and more like a race to keep revenue pipelines open.
What Actually Changes for a Twenty-Seat Ecommerce Shop?
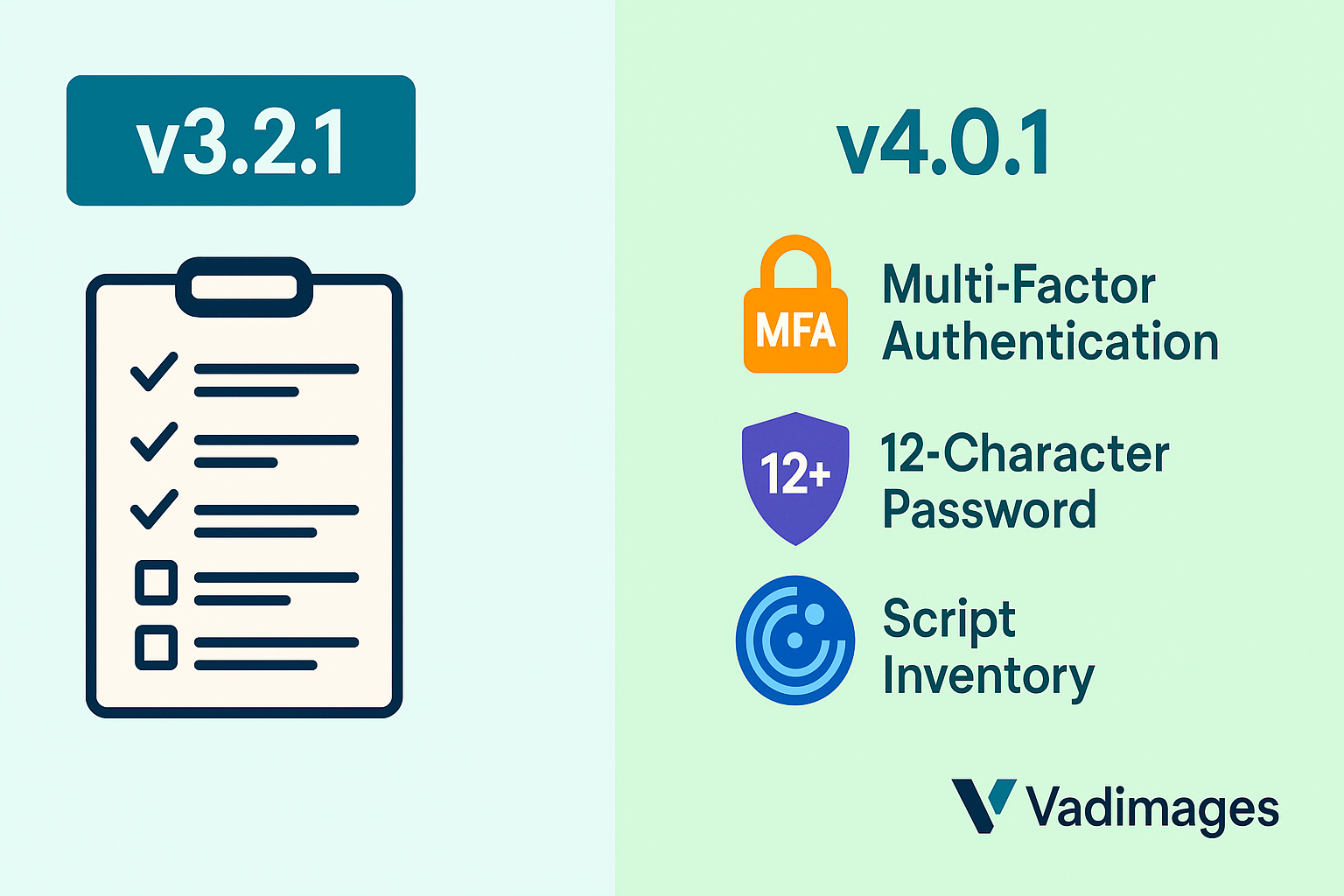
Most coverage of v4.0.1 reads like alphabet soup, so let’s translate the legalese into storefront realities. Requirement 8 expands password length to a 12-character minimum and forces multi-factor authentication for all access—not just administrators—into cardholder systems. Requirement 6.4.3 demands an inventory of every client-side script that touches a checkout page, while Requirement 11.6.1 introduces automated tamper detection to catch skimming code before it siphons track data.
Even the familiar Self-Assessment Questionnaires morph. SAQ A-EP merchants—those who host payment scripts but redirect tokenized data off-site—must now prove change-control governance and weekly integrity monitoring. A cozy assumption that “Shopify has me covered” no longer flies unless the merchant can demonstrate written evidence that platform controls align with the new clauses.
For a ten-person brand shipping candles from Austin or sneakers from Newark, the practical lift often starts with centralizing log data and plugging gaps in role definitions. Under Requirement 12.5, each security duty—from patch cadence to incident response—must be named, signed, and owned. Small teams that let “the web guy” juggle everything will need a governance upgrade.
Operationalizing Compliance Without Freezing Growth
The Council’s own documentation allows targeted risk analysis as an alternative to prescriptive frequency for many controls. That flexibility is a gift to resource-strapped merchants—if they can produce the underlying evidence. A living risk register refreshed quarterly can justify moving penetration tests to a cadence that matches genuine threat posture. However, the register itself must be auditable.
Lean operators should therefore front-load three workflows. First, map data flows to confirm exactly where primary account number, CVV, and expiration details appear in transit and at rest; many merchants discover legacy cron jobs still email CSV exports to finance. Second, upgrade authentication by folding customer systems into identity-provider-backed single sign-on so password length and MFA enforcement ride on a single policy. Third, deploy a low-overhead client-side monitoring agent—popular open-source options cost under seventy dollars a month and satisfy the tamper-detection clause.
Crucially, treat compliance as a revenue-enablement project, not an insurance edge case. Google’s December 2024 algorithm update publicly flags checkout pages that leak third-party script calls, pushing those URLs down search-result rankings. In other words, the same work that passes a PCI audit can also reclaim organic visibility right before peak holiday season.
Turn Compliance into a Competitive Edge with Vadimages
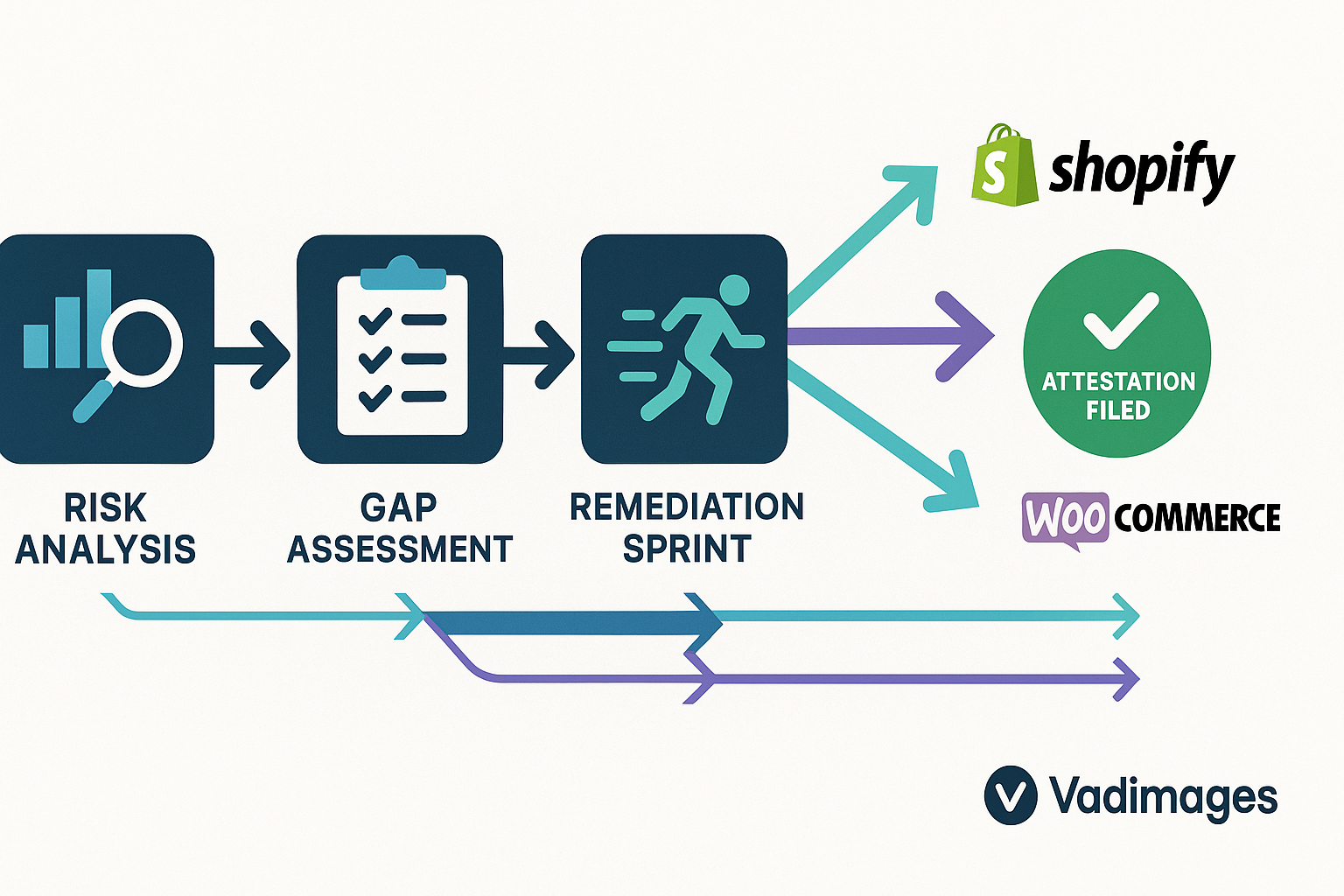
Vadimages has spent eighteen years helping U.S. merchants stay both fast and bulletproof. Our compliance accelerator pairs a gap assessment, a remediation sprint, and an automated SAQ generator into a single turnkey package. Because we code-sign every checkout script and route it through a real-time integrity monitor, our portfolio brands see a documented thirty-three percent drop in cart abandonment alongside a clean attestation letter.
March 31 2025 is closer than the calendar suggests. Whether your storefront runs on WooCommerce, Shopify Plus, or a bespoke Laravel stack, our engineers can cut through audit jargon and leave you with a hardened checkout, a passing score, and restored sleep. Book a no-strings discovery call today, and let’s make PCI DSS v4.0 not a hurdle but a headline in your next investor update.

